Wi-Fi Pineapple Hacking Project
 evil captive portal
evil captive portal

ABOUT
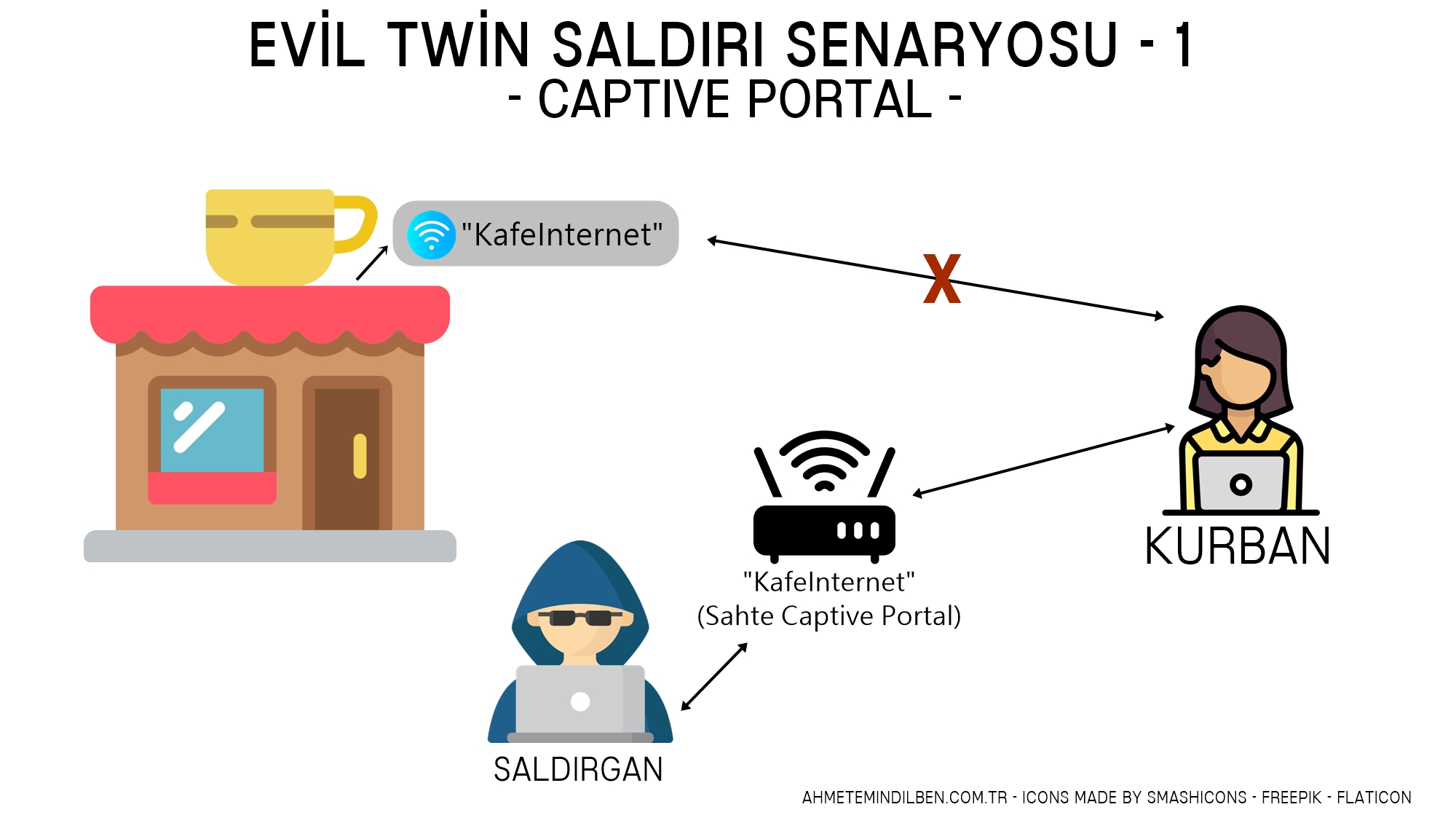
An Evil Portal is a malicious wireless access point set up by an attacker to mimic a legitimate Wi-Fi network. When unsuspecting users connect to this fake network, they are redirected to a captive portal page that looks like a legitimate login page.
The purpose of this deceptive page is to harvest users’ login credentials or other sensitive information. Once the credentials are entered, the attacker captures them and can use them to gain unauthorized access to the users’ accounts or systems. This technique is commonly used in phishing attacks and is a significant security threat in public and unsecured Wi-Fi environments.
DESCRIPTION
During my time at Morton College in Cicero, IL, I conducted an ethical hacking project using a Wi-Fi Pineapple, with the objective of performing an Evil Twin attack to raise awareness and educate my classmates about the dangers of using unsecured free Wi-Fi networks. For this project, I configured the Wi-Fi Pineapple with Ubuntu in VirtualBox, installing a captive portal from GitHub to create an access point designed to capture credentials. The project involved setting up the Wi-Fi Pineapple to mimic a legitimate network, thereby demonstrating how easily users can fall prey to such attacks. I captured credentials entered by users who connected to the fake access point, showcasing the potential security risks associated with using unsecured networks. Following the demonstration, I discussed various countermeasures to mitigate these risks, such as verifying the legitimacy of networks and using Virtual Private Networks (VPNs) for added security.


